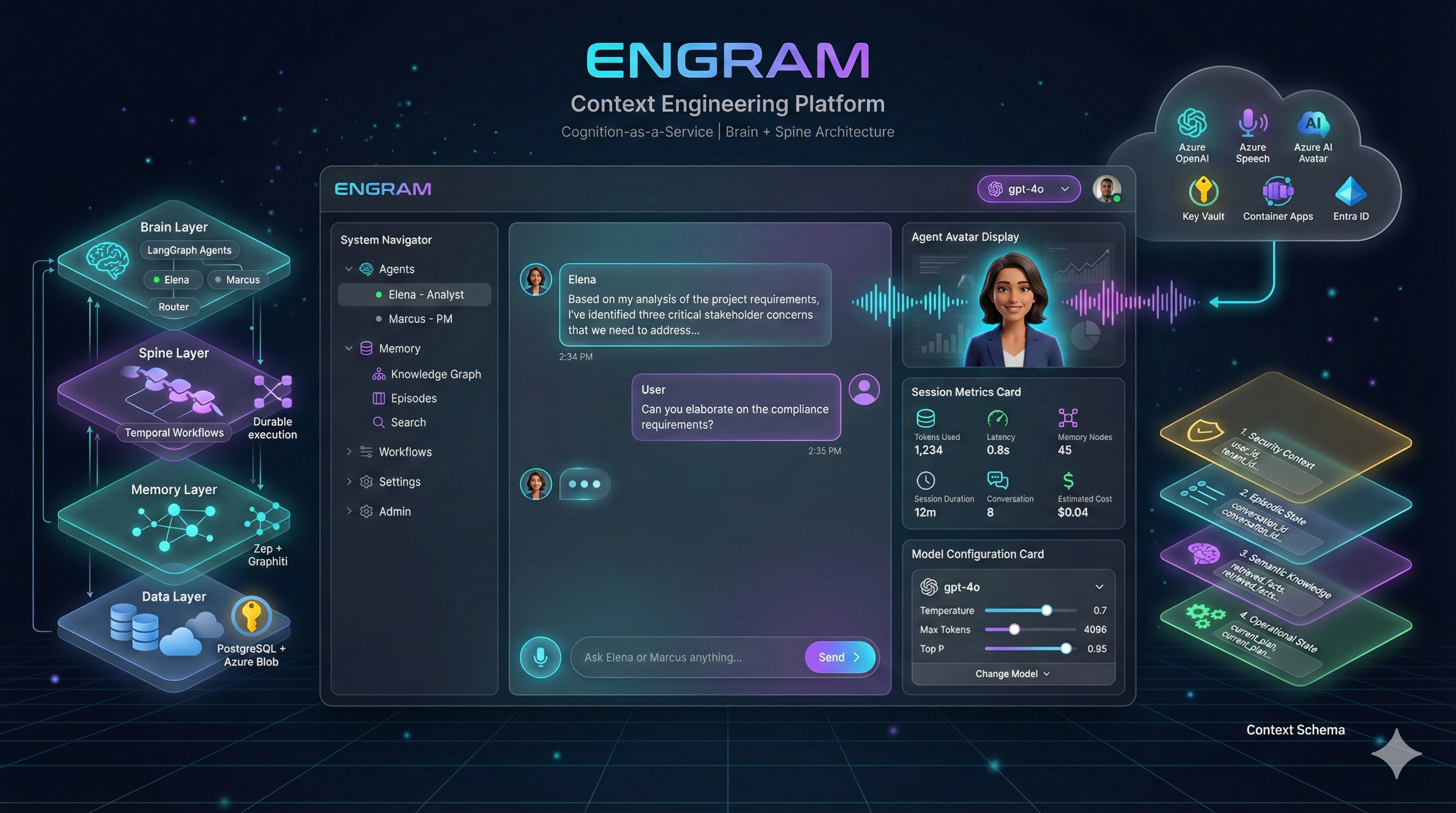
Engram Architecture
Engram implements a Brain + Spine architecture pattern, separating cognitive reasoning (Brain) from durable execution (Spine), with a persistent memory layer providing long-term knowledge storage.
Core Principles
1. Context Engineering over Prompt Engineering
Traditional prompt engineering focuses on crafting individual prompts. Context Engineering takes a holistic view:
| Aspect | Prompt Engineering | Context Engineering |
|---|---|---|
| Focus | Single prompt | Full context lifecycle |
| State | Stateless | Stateful across sessions |
| Memory | Limited context window | Unlimited via external memory |
| Security | Ad-hoc | Built into context schema |
2. Brain + Spine Separation
| Component | Brain (LangGraph) | Spine (Temporal) |
|---|---|---|
| Purpose | Reasoning & decisions | Durable execution |
| Lifecycle | Stateless functions | Long-running workflows |
| Failure | Retry at LLM level | Workflow-level recovery |
| Scale | Horizontal (replicas) | Workflow distribution |
Architecture Components
🧠 Brain + Spine Pattern
- Brain + Spine Story - The foundational architecture pattern
- Brain + Spine Diagram - Visual representation
📋 4-Layer Context Schema
- Context Schema Story - Complete guide to the 4-layer schema
- Security Context Architecture - Enterprise identity & attribution
- Context Schema Diagram - Visual diagram
🔐 Authentication & Security
- Authentication Analysis - Authentication deep dive
- Enterprise Auth Strategy - Production authentication
- Entra External ID - Azure CIAM integration
- Authentication Flow Diagrams - Visual flows
Architecture Highlights
Temporal Workflow Execution
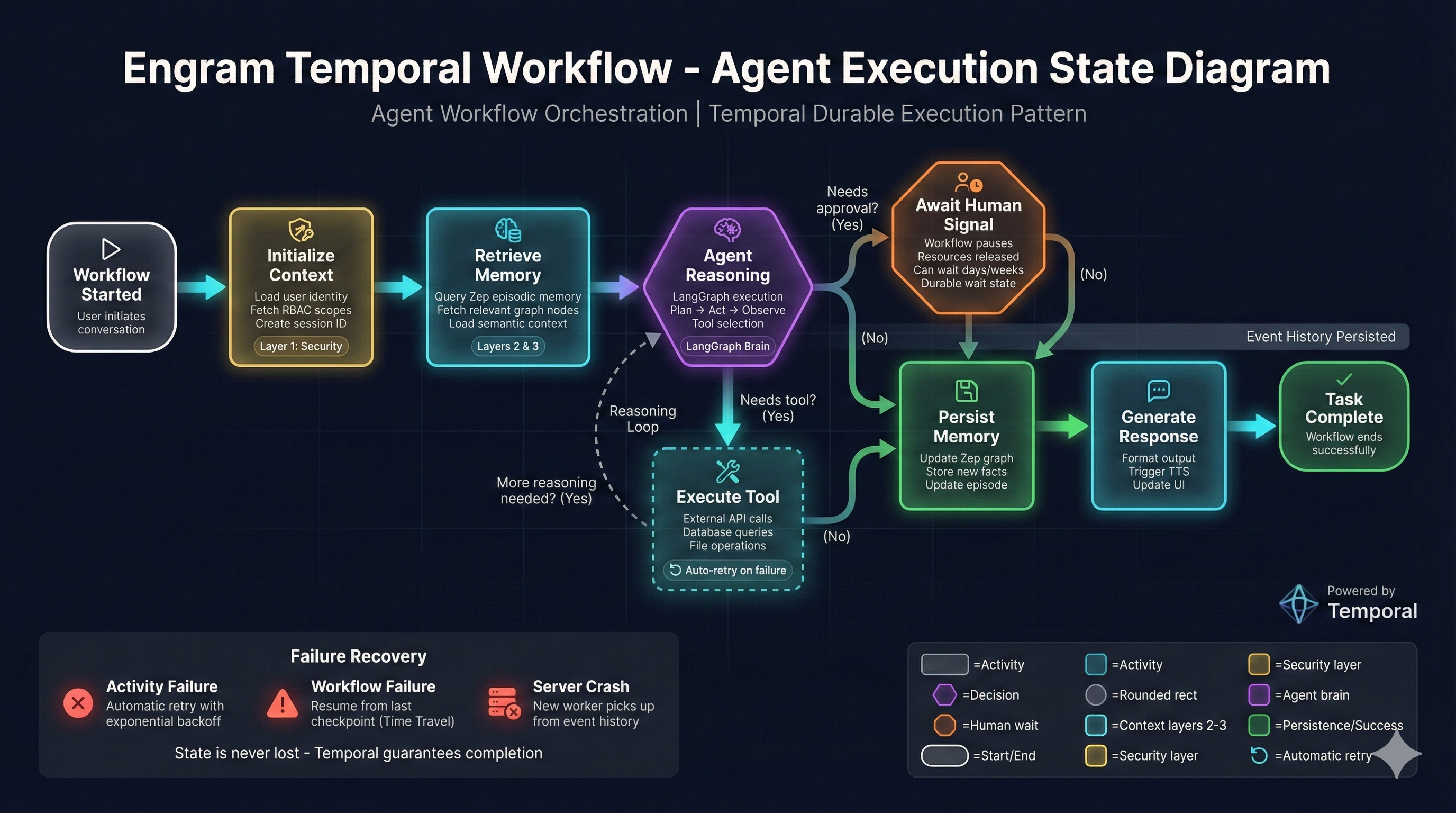
Layer 1: Security Context
SecurityContext is the foundation of enterprise security:
- Identity:
user_id,tenant_id,email,display_name - Permissions:
roles,scopes - Enterprise Boundaries: Tenant isolation, project scoping, RBAC
See: Security Context Architecture
Layer 2: Episodic State
Short-term working memory:
- Rolling window of recent turns
- Compressed narrative of history
- Prevents “Lost in the Middle” problem
Layer 3: Semantic Knowledge
Long-term memory pointers:
- Facts from knowledge graph
- Entity context and relationships
- Relevance scoring
Layer 4: Operational State
Workflow & execution state:
- Temporal workflow IDs
- Plan steps and tool state
- Human-in-the-loop support
- Cost tracking
Related Documentation
- Brain + Spine Pattern - Core architecture
- Context Schema - 4-layer context engineering
- Authentication - Security architecture
- Features - Feature-specific architecture
Next: Learn about Agent Personas or explore Features.
Table of contents
- Agent & User Isolation with Project-Based Access Control
- Azure AI Foundry Agent Service Integration
- Foundry Agent Service Integration - Impact Analysis
- Foundry Agent Service POC - Implementation Summary
- Foundry Thread Integration - Complete
- Using Foundry-Created Agents in Engram
- Elena Foundry Migration Guide
- Configuration Source of Truth Strategy
- Foundry Configuration Setup - Source of Truth
- Additional Foundry Features We Can Leverage
- Foundry Features Roadmap
- Elena Foundry Migration - Complete
- Elena Tool Endpoints - Configured
- Elena Avatar Configuration - Azure AI Foundry
- Elena Avatar Frontend Integration
- Multi-Agent Orchestration Research - Foundry Integration
- Microsoft 365 Integration Research - Teams & Outlook
- VoiceLive Avatar Integration
- VoiceLive Avatar Integration Complete
- Foundry IQ POC Implementation
- Foundry IQ Integration Summary
- AI Periodic Table Analysis
- AI Periodic Table Matrix
- Agent Personas
- Agentic System Maturity Assessment
- Authentication & Security Architecture
- Authentication Architecture Evolution
- Authentication Configuration Verification
- Comprehensive User Identity Flow Architecture
- Diagrams Directory
- Engram Authentication Architecture Analysis
- Engram Memory Architecture: Zep & Agents
- Engram System Architecture & Migration Context
- Enterprise Authentication Strategy: From POC to Production
- Enterprise Env Model
- Entra External ID Authentication
- Memory Enrichment Workflow: Sessions, Episodes, Stories, and Chat
- SecurityContext: The Foundation of Enterprise Identity & Attribution
- Sessions vs Episodes: Clarifying the Distinction
- System Navigator
- The 4-Layer Context Schema: A Complete Story
- The Brain & Spine: Engram's Context Engineering Architecture
- The Self-Enriching Workflow: Recursive Engineering
- User Identity Fixes Required
- User Identity Flow - Executive Summary
- VoiceLive Failsafe Token Generation
- VoiceLive Failsafe Token Generation - Breakthrough Summary
- VoiceLive v2 Architecture Diagram